On ICANN’s website and in their Annual Reports, they describe their mission “to help ensure a stable, secure, and unified global Internet. To reach another person on the Internet, you need to type an address – a name or a number – into your computer or other device. That address must be unique so computers know where to find each other. ICANN helps coordinate and support these unique identifiers across the world. ICANN was formed in 1998 as a not-for-profit public-benefit corporation with a community of participants from all over the world.”
From our perspective, ICANN is not a “public-benefit corporation” at all. They appear to make decisions that favor criminals and result in self-benefit because criminals are very likely providing a significant amount of the tremendous income that ICANN enjoys. ICANN does not seem to care that their domain naming goldmine, or use of proxy services to anonymously purchase domain names on someone’s behalf, or the lack of Registrar accountability, has poisoned the Internet and cost people of the world BILLIONS of dollars, along with immeasurable pain and suffering. (Internet fraud is a multi-billion dollar industry per year; according to many, such as the Insurance Information Institute.)
The Internet Corporation of Assigned Names and Numbers (ICANN) controls the Internet naming system, licenses the Registrars who sell Internet names, and makes a profit from every domain name that is sold. They are also MOST RESPONSIBLE for setting the rules to protect netizens around the globe and making sure those rules are followed by the Registrars. As a non-profit corporation they are required to publicly file a Form 990. According to their 2018 Form 990, ICANN had more than $469 Million dollars in net assets in 2018. ICANN earned nearly $92 Million dollars just from the sale of domain names through thousands of Registrars! In their annual report for Fiscal Year 2019, ICANN reported managing $464 Million dollars, of which $314 Million dollars came from the sale of new global top level domains. Göran Marby is currently the President and CEO of ICANN, as well as a member of their Board of Directors. According to their annual report of payments to Directors in 2019, Mr. Marby was paid $653,846 in salary, and $196,154 for at-risk pay, for a total of $850,000. This non-profit company is clearly overflowing with money!
How can we make such an egregious claim that this wealthy non-profit cares more about profit than internet safety? Let’s start with a very simple scam email containing the subject line “WORK FROM HOME.” (A TDS reader sent this to us without a working link connected to “SIGN UP.”) This email came from someone identified as Shen Yeh through the domain mailbox-gmail[.]com. This is such an OBVIOUS fraudulent effort to look like an email from Gmail. But this domain doesn’t belong to Google (the owner of Gmail.) This domain was first registered anonymously about 5 years ago, lapsed in use, and was then re-registered late last October, 2020. By contrast, gmail.com was registered more than 25 years ago by Google.
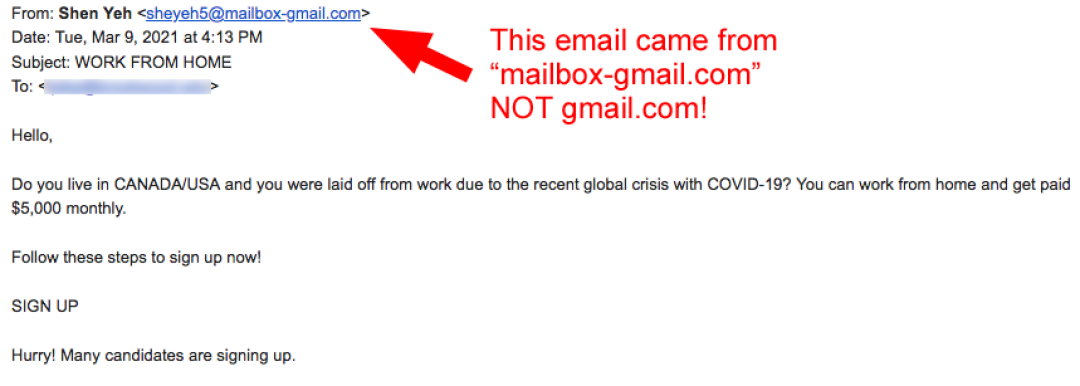
The content of the email says everything you need to know about its legitimacy. There is none. This email from March 9 is a fraud, preying upon those who are desperately looking for work. The name of this domain is so obviously a gmail-wannabe, infringing on Google’s copyright, and STRONGLY suggesting that it will be used for fraud. The registration of this domain name SHOULD HAVE raised alarm bells with any registrar! It should have been investigated and immediately shut down. Then it should have been added to a list of domain names that can never be registered by anyone BUT Google, the rightful owner of Gmail. But that’s not what ICANN or the Registrars care about because they make money when a domain name is registered and reregistered. Investigations of fraud are lengthy and require a citizen to report it first, assuming that he or she knows where and how to do that. It is often obtuse! Profit clearly comes before safe use of the internet by the World’s citizens.
Recently, we visited WHOIS DOMAIN SEARCH, a service that tracks every single domain registered every day. (Without paying for their service, visitors can download a list of the four most recent days of registration data.) At random, we downloaded a list of the 82,713 domain names that were registered on March 17, 2021. Amongst this list were the following 328 domains that stood out to us at a glance:
(This does not include the thousands of suspicious domain names that seem random, and are similar to domain names we routinely see used by cybercriminals in their daily effort to target people with malware.)
No doubt, some of the registered domain names found in the above group were legitimate, or were purchased speculatively for possible resale at a higher price. However, we’re absolutely certain that many of these names were purchased for the purpose of fraud and malicious intentions by cybercriminals. Examples of newly registered domain names that we believe are MOST LIKELY to be used for malicious purposes included:
Kayjewelerscreditcard.com (NOTE: Kay Jewelers, is based in Massachusetts and uses Kay.com. It was registered 25 years ago to Sterling Jewelers. This look-alike domain was registered anonymously last week and is hosted on a server in Wales, UK.)
On March 16, 2021, 92,968 domains were also registered. It took us a mere 5 minutes to find three domains that we strongly believe will be used for fraudulent purposes:
To demonstrate the abuse, possible fraud and confusion related to the current rules around domain registration, let’s take a closer look at the newly registered domain HawaiiNationalBankOnline.com. We found a very robust banking website using this domain just a few days after it was registered. As we scrolled through pages, however, we found some things that were suspicious…
In the bottom left corner of their home page, they described themselves as “Fidelity Bank.”

Errors in grammar and capitalization, such as “Banks Of Hawaii team provides independent advice based on established research methods.”
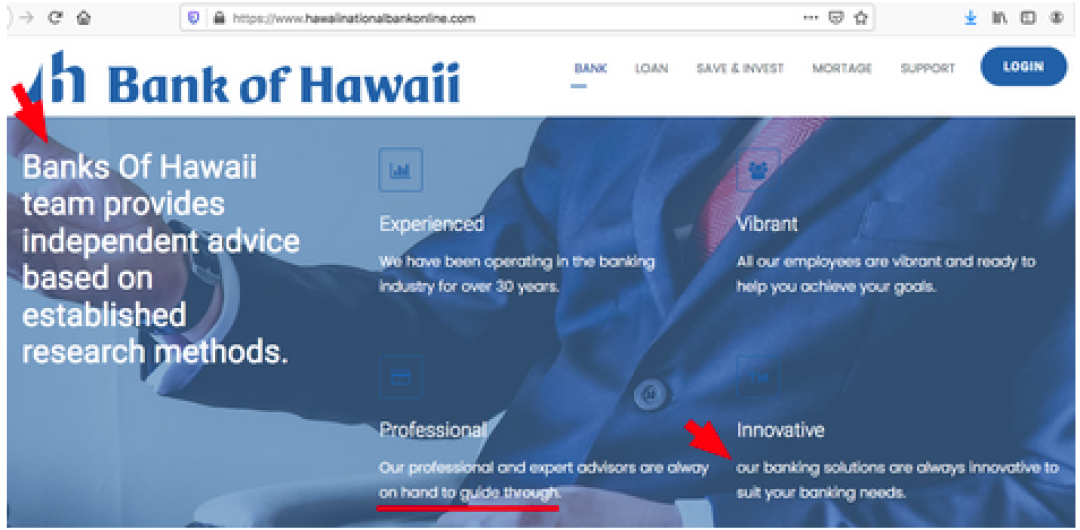
2. “Hawaii National Bank Online” is using the same logo and name as “Bank of Hawaii.” Bank of Hawaii uses the domain boh.com and this short domain has been registered to them for more than 25 years.
Based on these oddities, we conducted an image search for one of the “Team Advisors” of HawaiiNationalBankOnline.com, and shown in this screenshot as Peter Davidson Jnr, Chief Financial Officer. This is where the insanity begins as we found ourselves at the precipice of a deep dark rabbit hole.
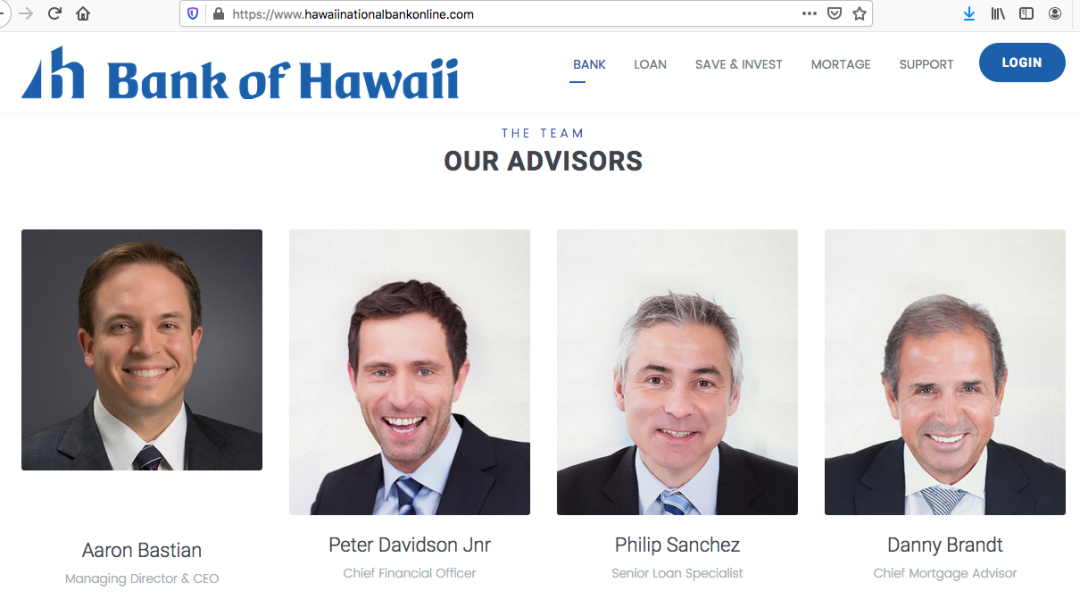
We found this exact same photo of “Peter Davidson Jnr” (along with other photos from this team) on MANY other websites with different names and purposes. They included the names:
It seems clear to us that the photo used for Peter/Morgan/Stephen/Amir is very likely a stock photo, as are most or all of the other photos we found on these dozens of websites. This, along with the grammatical and punctuation errors, suggests that these sites may not be trustworthy. It’s important to remember that we started down this rabbit hole because we found that a domain associated with banking was registered just last week.
ICANN, the keeper of the domain keys, is filthy rich because of the sale of domains and licensing of Registrars. Their strategy has been to do everything possible to create new domains to sell and make money. But they completely ignore their responsibility to the public! For example, why do they allow domains to be purchased anonymously? Why don’t they create better rules about selling domains that are designed to protect the public? Why don’t they spend some of their millions of dollars to establish a large team of people who are responsible for making sure that Registrars comply with rules? Better yet, why don’t they investigate the purchase and use of fraudulent domains and shut them down? Why don’t they prevent domains that infringe on copyrights of legitimate businesses from ever being released to anyone but the rightful owners of those names? By now, the answer should be clear. It’s because they don’t care about the public. They care only about making money, something that cybercriminals are very happy to do for them.
Via The Daily Scam.